Windows Events log to SigNoz
Overview
If you are using a Windows environment, you can stream Windows Event Logs to SigNoz using OpenTelemetry Collector. Monitoring specific Event Log sources, known as Channels, can be done using the Windows Event Log receiver configured in the OpenTelemetry Collector configuration file.
Key channels typically monitored include:
- Application: Logs events related to applications running on the system.
- Security: Records security-related events such as login attempts and resource access.
- System: Captures events related to system components, drivers, and services.
Prerequisites
- Microsoft User account with permissions to access Event Log and Services.
Setup
Step 1: Install OpenTelemetry Collector
Install OpenTelemetry Collector as an agent by following the SigNoz Cloud Installation Documentation.
Step 2: Configure windowseventlog receiver
Add windowseventlog Receiver
Modify the config.yaml file to include the windowseventlog receiver for monitoring application and system logs:
receivers:
windowseventlog/application:
channel: application
windowseventlog/system:
channel: system
Update Pipelines Configuration
In the same config.yaml file, update the pipelines section to include the windowseventlog/application and windowseventlog/system receivers:
service:
pipelines:
logs:
receivers: [windowseventlog/application, windowseventlog/system]
processors: [batch]
exporters: [otlp]
Save the changes and restart the OpenTelemetry Collector.
Output
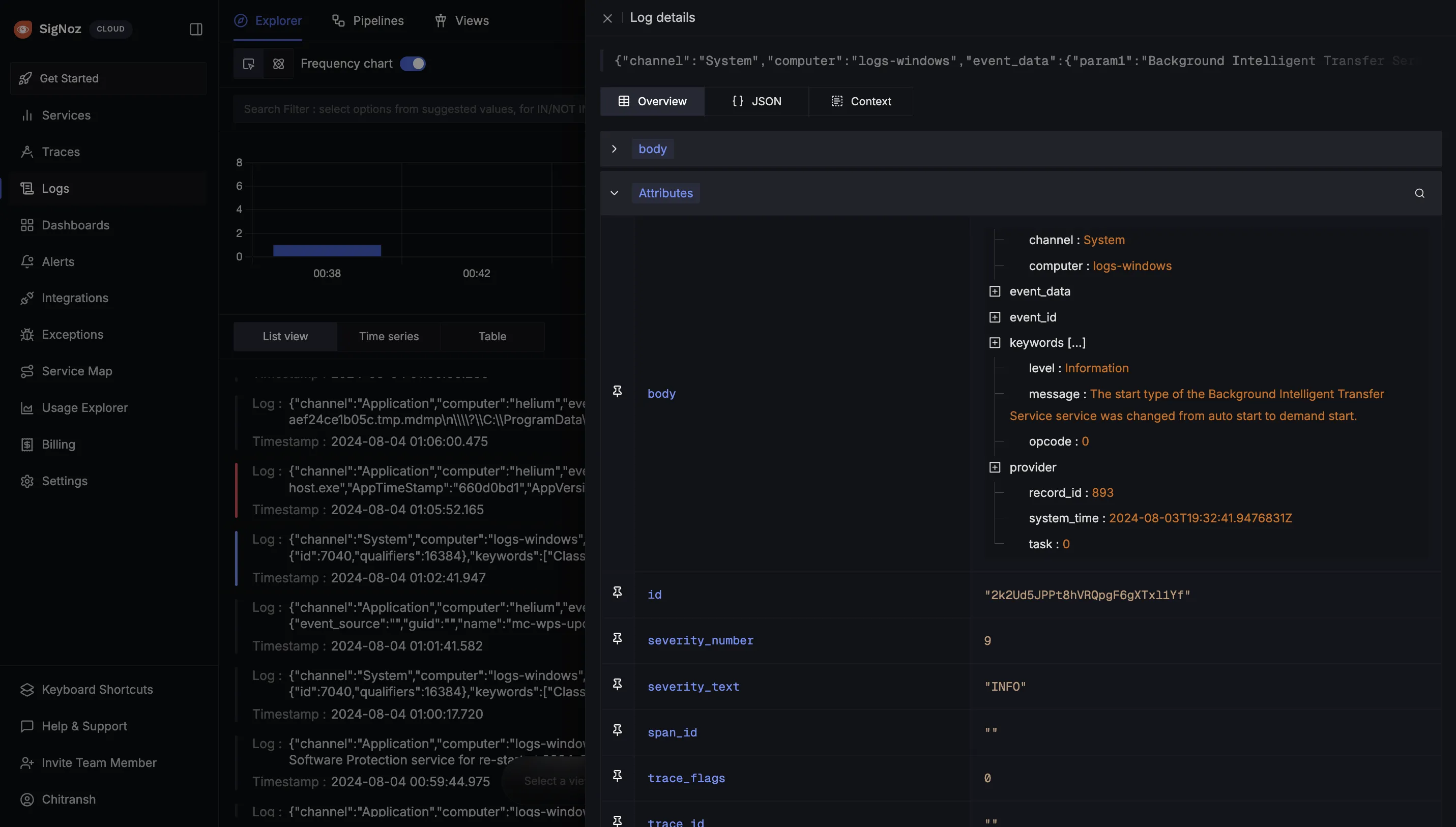
This is what the typical output will look like with the configurations made above:
Application Log
{
"body": "{\"channel\":\"Application\",\"computer\":\"logs-windows\",\"event_data\":{},\"event_id\":{\"id\":16384,\"qualifiers\":16384},\"keywords\":[\"Classic\"],\"level\":\"Information\",\"message\":\"Successfully scheduled Software Protection service for re-start at 2024-08-10T18:52:44Z. Reason: RulesEngine.\",\"opcode\":\"0\",\"provider\":{\"event_source\":\"Software Protection Platform Service\",\"guid\":\"{E23B33B0-C8C9-472C-A5F9-F2BDFEA0F156}\",\"name\":\"Microsoft-Windows-Security-SPP\"},\"record_id\":750,\"system_time\":\"2024-08-03T19:29:44.9757970Z\",\"task\":\"0\"}",
"id": "2k2Ud5JPPt8hVRQpgF6gXTxl1Yd",
"timestamp": "2024-08-03T19:29:44.975797Z",
"attributes": {},
"resources": {},
"severity_text": "INFO",
"severity_number": 9,
"span_id": "",
"trace_flags": 0,
"trace_id": ""
}
System Log
{
"body": "{\"channel\":\"System\",\"computer\":\"logs-windows\",\"event_data\":{\"param1\":\"Background Intelligent Transfer Service\",\"param2\":\"auto start\",\"param3\":\"demand start\",\"param4\":\"BITS\"},\"event_id\":{\"id\":7040,\"qualifiers\":16384},\"keywords\":[\"Classic\"],\"level\":\"Information\",\"message\":\"The start type of the Background Intelligent Transfer Service service was changed from auto start to demand start.\",\"opcode\":\"0\",\"provider\":{\"event_source\":\"Service Control Manager\",\"guid\":\"{555908d1-a6d7-4695-8e1e-26931d2012f4}\",\"name\":\"Service Control Manager\"},\"record_id\":893,\"system_time\":\"2024-08-03T19:32:41.9476831Z\",\"task\":\"0\"}",
"id": "2k2Ud5JPPt8hVRQpgF6gXTxl1Yf",
"timestamp": "2024-08-03T19:32:41.9476831Z",
"attributes": {},
"resources": {},
"severity_text": "INFO",
"severity_number": 9,
"span_id": "",
"trace_flags": 0,
"trace_id": ""
}
Last updated: December 18, 2024
